What did the ransomware attacker do...
24
10
What did the ransomware attacker do for 3 hours from the start of the attack to the encryption?: Real record, high -speed ransomware attack
Sophos threat researchers have found a new kind of ransomware that attacks at a surprising speed.This ransomware is made by Python, targeting the "VMware ESXI" server and virtual machine (VM).This combination may not be very careful, and may cause a serious threat to many environments.
Many cyber criminals move around the ransomware after moving around the victim's system for a long time.However, the ransomware discovered this time launched a "super -high -speed" attack in just a few hours.
"SOPHOS has been the fastest ransomware attack," said Sophos's Andrew Brant (chief researcher).Some of the incidents he investigated took only three hours from infringement to encryption.
iStock.com/ismagilovIn the case of the investigation, the attack began at 0:30 am.
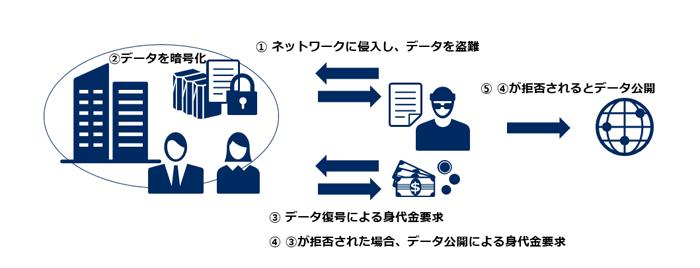
At that time, the attacker has a TeamViewer account of the system user.This account had domain management authority and qualification information.
It took less than 10 minutes for the attacker to aim for the ESXi server and use Famatech's "Advanced IP Scanner" to smell the target.The ESXI server has an active shell programming interface, so it is likely to be vulnerable.
Next, the attacker installed the remote access tool "Bitvise" on the administrator's PC.This enables access to the ESXi system containing VM virtual disk files.At 3:40 am, ransomware was deployed and the file was encrypted.
According to Brandt, the case had some luck on the attacker.The damaged IT team has repeatedly enabled / disabled server shell interfaces, and may have been effective when attacked.So the attack was much easier.
"You should disable" ESXI SHELL "except for regular maintenance such as patch installation. You can disable ESXI SHELL using the control or software management tool of the server control."
The ESXI server is an attractive target for cyber criminals because you can attack multiple VMs that may be running business critical applications and services at once."Attacks on the hypervisor can be high -speed and very devastating. Ransomware attack activities such as DarkSide and Revil make the ESXi server target for attacks."
"Administrators who operate hypervisors such as ESXI need to follow the security best practices. It includes the use of passwords that are difficult to attack Blue Force and forced to apply multi -factor authentication" (Brandt).
SOPHOS offers ransomware -related materials such as tactics, techniques, and procedures (TTPS: Tactics, Techniques, and Procedures).VMware provides guidance on ESXI protection.