Thinking about the relationship bet...
16
04
Thinking about the relationship between "blocking" and MVNOs, and the secrets of communication: MVNO's deep story (page 1/2)
On April 23, 2018, NTT Group companies (NTT holding company, NTT Communications, NTT DoCoMo, NTT Plala) are jointly named and have a policy of "blocking" to prevent browsing of sites dealing with pirated comics etc. Announced. In this regard, I would like to think about "secrets of communication" with carriers including MVNOs.
Does Carrier Blocking Affect MVNOs?
On April 13, 2018, at the government's "Intellectual Property Strategy Headquarters / Crime Countermeasures Ministerial Conference", a site dealing mainly with "pirated versions" centered on cartoons (contents of third parties without permission) It was announced that it is appropriate for telecommunications carriers such as MVNOs, carriers, and ISPs to voluntarily perform "blocking" that makes it impossible to browse the distribution site). In response to this, on April 23, NTT Group companies jointly announced that they would implement blocking for specific sites. This issue has been covered in the news, so many of you may be familiar with it.
According to NTT Group's announcement, this blocking will also apply to DoCoMo's contract. In addition, DoCoMo responded to a question from the media that "this blocking does not affect the MVNO."
There are several possible methods for blocking, but according to the above article, we are planning to introduce a technology called "DNS blocking". Generally, when a smartphone accesses a Web server, it inquires about the IP address of the server to access the DNS server installed in the carrier.
The DNS server of the carrier makes an inquiry to the DNS server on the Internet, and by responding to the smartphone with the IP address found by it, the smartphone can start communication with the target Web server using the IP address. increase. However, when DNS blocking is introduced, even if you try to access the website to be blocked, the DNS server of the carrier does not make an inquiry to the DNS server on the Internet, and "the server does not exist" or "the server does not exist" or " It makes a fake response such as "fake IP address". As a result, the target Web server cannot be accessed from the smartphone, and "blocking" is established.
Flow when normal communication and blocking are performedWhen the smartphone connects to the mobile phone network, the device in the mobile phone network notifies the smartphone of the information of the DNS server used by the smartphone. If you have a DOCOMO contract, when you connect to the mobile phone network, you will be notified to use the DNS server prepared by DOCOMO. It is expected that the above-mentioned mechanism will be applied to this DNS server.
Recently, almost all MVNOs operating as "cheap smartphones" are connected to carriers by the method of "L2 connection". When making an L2 connection, the device operated by the MVNO is responsible for notifying the smartphone of the DNS server. Generally, the DNS server notified by the MVNO is prepared by the MVNO itself, not by the carrier.
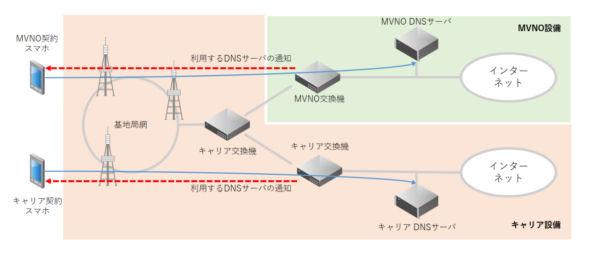
Even if the MVNO rents equipment from DoCoMo, the DNS server used is prepared by MVNO instead of DoCoMo, so even if there is something in the DoCoMo DNS server, it will not be affected. Become.
Mobile network and DNSOf course, if the MVNO tricks its DNS server, blocking will be applied to that MVNO subscriber. This time, NTT Communications, which operates OCN Mobile ONE, has announced that it will implement blocking, but in this case, OCN Mobile ONE subscribers will be notified that they will use the DNS server prepared by NTT Communications. Imagine something happening to that DNS server.
By the way, what happens to secondary MVNOs that operate by renting equipment from other MVNOs (MVNEs)? In principle, the secondary MVNO is also an independent telecommunications carrier, and the service provision contract with the user is concluded by the secondary MVNO itself. Whether or not the secondary MVNO will block will be determined independently of the MVNE.
However, most secondary MVNOs do not have their own equipment and use MVNE equipment to provide communication services. In the cases I understand, in such cases, it is thought that the DNS server prepared by the MVNE will be used, and whether or not the MVNE is blocked depends on the MVNO provided with the equipment by the MVNE. There is a possibility that it will be lost.
However, this is only if you do not make any changes to the existing equipment. In principle, it is possible to change the DNS server that notifies by APN etc., so it is considered that the presence or absence of blocking can be decided by the judgment of the secondary MVNO regardless of whether or not the MVNE is blocked. However, for that purpose, it is necessary to prepare new equipment and change the settings, and it is necessary to coordinate between the MVNE and the secondary MVNO in terms of how to bear the cost and labor. It seems that.
What is the secret of communication?
By the way, as already pointed out in a number of news and comments from experts, blocking, which is the topic of discussion this time, raises the issue of how to balance it with the "secret of communication". In order to block, it is necessary for the carrier to look at the contents of the communication in some way and decide whether it should be blocked, and it is pointed out that this violates the user's "secret of communication". is.
In Japan, mobile phone services provided by MVNOs and carriers are classified as "telecommunications business" and are regulated by the Telecommunications Business Law. The Telecommunications Business Law stipulates that "secrets of communication" should not be invaded.
Article 1 of the Telecommunications Business Law is the purpose of the law, Article 2 is the definition of terms, and Article 3 is the provision regarding the prohibition of censorship. The fact that the secrecy of communications is listed as an independent item in Article 4 immediately after that indicates that the secrecy of communications is considered to be particularly important in the Telecommunications Business Law.
Then, what kind of act is "infringing the confidentiality of communications"? It is said that there are three types of "knowledge," "leakage," and "theft."
I think it's easy to understand that "leakage" and "theft" are bad things. However, in reality, it is necessary to be aware that even "knowing the secret of communication (knowledge) by a third party" is an infringement of the secret of communication.
Let's apply this type to the blocking pointed out this time. To block, the carrier must first know if the user's communication falls under the blocking target. This is considered to be "knowledge". On top of that, it is thought that it will be in the form of "stealing" due to the act of blocking.
One thing to keep in mind here is that if a carrier implements blocking, the privacy of communications is not limited to communication with the blocking website. This is because we see (know) every communication of every user to identify whether that communication is blocked. One of the blocking issues is that the confidentiality of communications is compromised even for the communications of good users who have not browsed any pirated sites.
What if it's okay to touch the secrets of communication?