Easy way to prevent unauthorized us...
26
06
Easy way to prevent unauthorized use by hitting a tight key to the LAN terminal
Your LAN terminal is dangerous!maybe?
Your LAN terminal is dangerous!maybe?
Desktop PCs and stationary laptops are mostly LAN terminals.
Needless to say, the terminal is used to insert a LAN cable and connect to the Internet, but this LAN terminal is very easy.
It can be said that there is almost no need to change it to a different PC because it can be removed just by pinching the nails and pulling it.
It is common to apply a password or biometric authentication to make it impossible for anyone other than the user to log in, or to limit the change to the machine, but the LAN terminal may be defenseless.many.
It is also dangerous for a PC to be able to use the USB terminal, which is the entry and exit of the data.If you have malicious intent, you can infect malware via a USB memory, and above all, you can take away highly confidential data via USB.
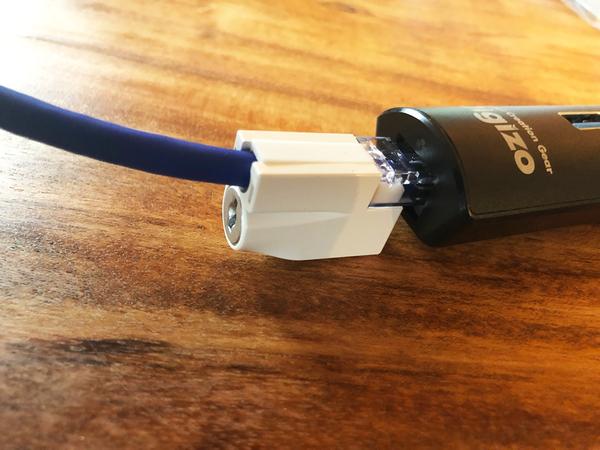
It is difficult to find a person who has not put a password on a personal PC, but the very minorities who have some security measures on the LAN terminals and USB terminals.Is the LAN terminal that can be connected to the internet or the USB terminal that is the entrance to the data so defenseless and good?
A tragedy that happens just to leave the LAN terminal!
Let's think of a tragedy that could happen just to leave the LAN terminal unprotected.Just in case, all of the following cases are fiction and consider the worst case.
Occurs at the museum?Viruses scattering case
In City A, the local museum is open to make the townspeople and tourists know the local history.
The local museum has a PC search and a PC for guidance in the museum.The LAN cable was inserted to the LAN cable on the PC to connect to the line contracted at the museum.
On the other hand, the USB terminal is only used only when adding or editing materials, and is almost "vacant" during the opening hours.PCs are basically available to anyone.Who can monitor what is doing what is doing what is doing what is doing what is doing what is doing what is doing what is doing what is doing what is doing what.The culprit turned his eyes on it and inserted a USB memory with malware.
Before the staff knew, the PC of the local museum had been submitted to malware.Except for the criminal video shown in the security camera, there is no evidence and it is difficult to identify.The staff in charge of the Local Museum has been charged for lack of management.
Suddenly writing a crime!?
A company that is allowed to use BYOD (business use of private devices), and B uses a desktop PC brought in.The wired LAN cable is inserted, but in B's workplace, a unique IP address is distributed for each individual, and basically one person uses the same LAN cable.
The criminal C, who does not like B's promotion, uses B's LAN cable secretly after returning to the employee.He posted a criminal notice and a URL distributing a criminal notice and a preliminary circle on his PC on SNS and Internet bulletin boards.
A later police survey revealed that the IP address was managed by Mr. B, but the MAC address (address on the LAN terminal side of the device) is different from what B usually uses.However, I don't know who the MAC address is on the PC.Mr. B has been heard in detail as a reference person.
Normally, this does not happen first, but it is possible to use other people's LAN terminals and USB terminals to do wrong.Putting a password on the PC is also the purpose of preventing the data recorded inside and the device itself from the abuse.It is difficult for someone to touch your PC and access the internal data without permission, but it may be common sense to passwords.
Nevertheless, it is strange that the USB terminal and LAN terminal are left unprotected.This is the security -related product series sold by Princeton.