Don't forget to take measures for A...
06
12
Don't forget to take measures for ASCII.jp port scanning inside the LAN!
If you do product training to sales and technical people in various partner companies, you will have various questions every time.The other day, when I was doing product training, "Do I need a host -based invasion prevention function (IPS) for PCs? End users do not need extra functions, so I don't want to put them in if possible.I was asked the question.
Because it is a function mounted on the product, it is of course installed because it is necessary for security measures.Therefore, the reply is "It is a function necessary to prevent virus infection into a PC via LAN", but there are some related matters, so this time from this host -based invasion prevention function.I want to delve into the story.
Host -based IDS and IPS
I think many companies are enrolling / entering the room at the entrance of the office, but it will be difficult to completely prevent unauthorized intrusion.Therefore, I think that there are cases where security cameras are installed in the office, and in some cases, guards are dealt with and deal with illegal enrollment.
The same is true for internal LAN security.For safety, it is desirable to use not only personal fire walls introduced earlier, but also functions called host -based intrusion (IDS) or invading (IPS).
The host -based IDS monitors the network connection that comes into the PC (host) and determines unauthorized connection.You may think that the detection of fraudulent invasion is possible with a firewall, but in fact firewall alone cannot be completely prevented.This is because the firewall allows the connection to the communication from the authorized protocol / IP address (for example, in -house IP address), even if the communication is prevented.
Consider the case where you can spread the infection to other PCs via internal LAN from an in -house PC that has been infected with viruses.Viruses make a large number of connections to other PCs in the company in a short time to try virus infection.Even in this case, it is not possible to determine whether the connection is malicious in a firewall that only allows the connection according to the permission port setting.
In such cases, the host -based IDS is appropriately finding whether communication to the host is a connection for virus infection.Analyze the connection pattern and notify users according to the settings for suspicious connection patterns.
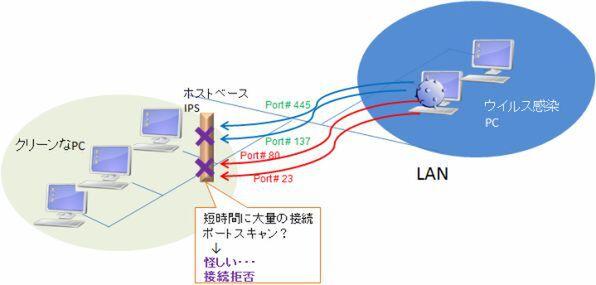
In the firewall, simply establish / reject the connection according to the permit / rejection list, and do not judge the connection pattern.
However, even if the host -based IDS issues a notification, it will be difficult for users to judge whether the content of the notification is really dangerous.Even if you contact the administrator, you may not be able to respond immediately, and in the meantime, virus infection may spread.
Therefore, when the suspicious connection is detected, the host -based IPS has the function of "maybe a legitimate connection, but keep it suspicious for safety."Detects a suspicious connection pattern and refuses the connection according to the settings.
Invasion prevention (IPS) detects the connection pattern and blocks the connection with a "do not pass suspicious" policy.
It is a targeted attack that increased the recognition rate in the second half of 2011, but the malware used for the attack will search for PCs in the LAN once and collect information, or port scans in the LAN.。In this way, they penetrate with the vulnerable of another PC, obtain the necessary information, send them to the attacker, or open the backdoor to allow external control.
Port scanning in the LAN, use vulnerabilities to expand infection and obtain information
In this way, most of the malware active in the LAN uses port scanning methods in the LAN to expand infection and steals in -house information, so measures for Port Scan in the LAN for network managers in the company.You can think of it as a must.
| TCPコネクトスキャン | TCPポートを対象とした手法で、3WAYハンドシェイクと呼ばれるSYN-SYN/ACK-ACKのシーケンスを実行し、ターゲットポートにおいてTCPコネクションを確立できるかどうかで状態を確認する。 |
|---|---|
| SYNスキャン(TCPハーフスキャン) | TCPポートを対象とした手法で、コネクションは確立せずに、ターゲットポートの状態のみを確認する。接続する代わりにターゲットポートに対してSYNパケットを送り状態を確認・ターゲットポートからSYN/ACKを受信した場合のポートはLISTEN状態・ターゲットポートからRST/ACKを受信した場合のポートは非LISTEN状態 |
| UDPスキャン | UDPではコネクションは確立できないので、ターゲットポートにパケットを送り、応答がなければACTIVEと判断。「ICMP port unreachable」が戻れば非ACTIVEと判断する |
Use the firewall and IPS/IDS together
As mentioned above, the firewall alone only performs the connection control by the permission list / rejection list, so we do not determine whether it is a suspicious connection.For this reason, viruses and attackers who are trying to infect LAN infections have tried to connect to a PC with a port scan and understand the status of the PC.I will try to install it using the weak part.
From the viewpoint of the spread of the LAN virus due to targeted attacks, the prevention of information theft, and the measures to prevent information theft, we would recommend using the host -based IDS or IPS along with the firewall.
Make the most of the functions installed in the security products that are being introduced, and keep the safety in the LAN.In addition, when selecting security products, it is strongly recommended to focus on the functions that can take network security measures from the viewpoint of protecting PCs, servers, and saved information on the LAN.increase.
Fusecure Co., Ltd. Technology & Service Department Product Expert In 2008, joined Fusecure.He is mainly in charge of technical support for Linux products to his partner.